In today’s digital-first world, secure customer authentication isn’t just a technical necessity – it’s a frontline defense for businesses. Every login, every transaction, and every customer interaction presents both an opportunity and a risk. Data breaches, account takeovers, and clunky authentication processes don’t just frustrate users – they erode trust, drive away customers, and hit revenue hard.
That’s where Customer Identity and Access Management (CIAM) steps in. Unlike outdated login systems, CIAM isn’t just about keeping bad actors out—it’s about creating seamless, secure experiences that keep customers engaged while fortifying businesses against evolving cyber threats. In this blog, we’ll break down how CIAM drives business success, enhances customer experience, and the best strategies for implementing it effectively.
What is CIAM & Why It Matters for Business Growth
Defining CIAM: A Focus on Authentication, Security, and User Access
CIAM, or Customer Identity and Access Management, is a specialized branch of identity access management (IAM) that focuses on securely managing and verifying user identities. CIAM solutions ensure that customers can seamlessly access digital services while protecting sensitive information from unauthorized access.
Key components of a CIAM platform include:
- User authentication (passwordless login, biometrics, multi-factor authentication)
- Access control (role-based access, risk-based authentication)
- Customer identity management (single sign-on, social logins)
- Compliance support (GDPR, CCPA adherence)
The Role of CIAM in Digital Transformation and Business Scalability
A well-implemented CIAM strategy enables businesses to:
- Provide seamless and secure access to customers
- Enhance user experience with seamless authentication, personalized interactions, and progressive profiling to drive engagement and long-term retention.
- Reduce fraud risks and unauthorized access
- Scale secure authentication processes as user bases grow
The Business Risks of Weak Authentication Systems
Failing to implement a robust CIAM solution can lead to:
- Account takeovers (ATO) and credential stuffing attacks
- High churn rates due to frustrating login experiences
- Regulatory fines for non-compliance with data privacy laws
- Loss of trust and damage to brand reputation
Unlocking Growth: Key Business Benefits of CIAM Solutions
Enhanced Security & Fraud Prevention
Account takeovers and credential stuffing attacks are rising, with hackers exploiting weak passwords and reused credentials. A strong CIAM platform mitigates these risks by implementing:
- Multi-Factor Authentication (MFA)
- Risk-based authentication to assess suspicious login behavior
- Biometric and passwordless authentication
Frictionless & Secure Authentication: Balancing Security and User Experience
Businesses must balance security and convenience to prevent fraud while ensuring seamless access. CIAM solutions achieve this by implementing:
- Adaptive authentication, which adjusts security measures based on user risk levels.
- Social logins (Google, Facebook, Apple ID) for faster access.
- Single sign-on (SSO) to reduce login fatigue across multiple platforms.
- Passwordless authentication using biometrics, passkeys, or one-time authentication links, enhancing security while streamlining user experience.
By reducing login friction without compromising security, CIAM platforms improve user satisfaction and minimize abandoned sessions.
Boosting Customer & Employee Productivity
Reducing Helpdesk Requests for Password Resets
IT support teams spend a significant amount of time handling password resets. A well-designed CIAM implementation drastically reduces these requests by offering:
- Self-service password recovery options
- Secure authentication alternatives (MFA, biometrics)
Streamlining Authentication for Workforce and B2B Users
CIAM solutions extend beyond customers to support workforce and partner authentication, ensuring efficient access control for employees and B2B stakeholders.
Personalized Customer Experiences
A well-implemented CIAM strategy does more than protect businesses—it enhances the customer experience by:
- Reducing login friction with progressive profiling and social sign-ins.
- Leveraging identity-driven insights to create personalized shopping journeys.
Strengthening customer trust with secure, transparent authentication.
Compliance & Regulatory Adherence
With evolving data privacy regulations like GDPR, CCPA, and PCI DSS, businesses must prioritize secure authentication and data handling practices. A CIAM solution ensures compliance by:
- Enforcing strong authentication policies (MFA, passwordless logins).
- Providing user consent management for transparent data handling.
- Offering audit logs and reporting tools to meet regulatory requirements.
Best Practices for Implementing a CIAM Solution
Selecting the Right Authentication Mechanisms
A robust CIAM implementation should include:
- Adaptive MFA for varying risk levels
- Passkeys and passwordless options
- Social and third-party logins
Optimizing Authentication Workflows for Conversion & Retention
Businesses must balance security with user experience (UX). Strategies include:
- Minimizing authentication steps for low-risk logins
- Offering biometric and SSO options
- Analyzing user behavior to refine authentication flows
As cyber threats evolve, AI-driven security measures and continuous authentication improvements are crucial for maintaining a competitive edge.
Why Descope is a Smart CIAM Solution for Growth-Focused Businesses
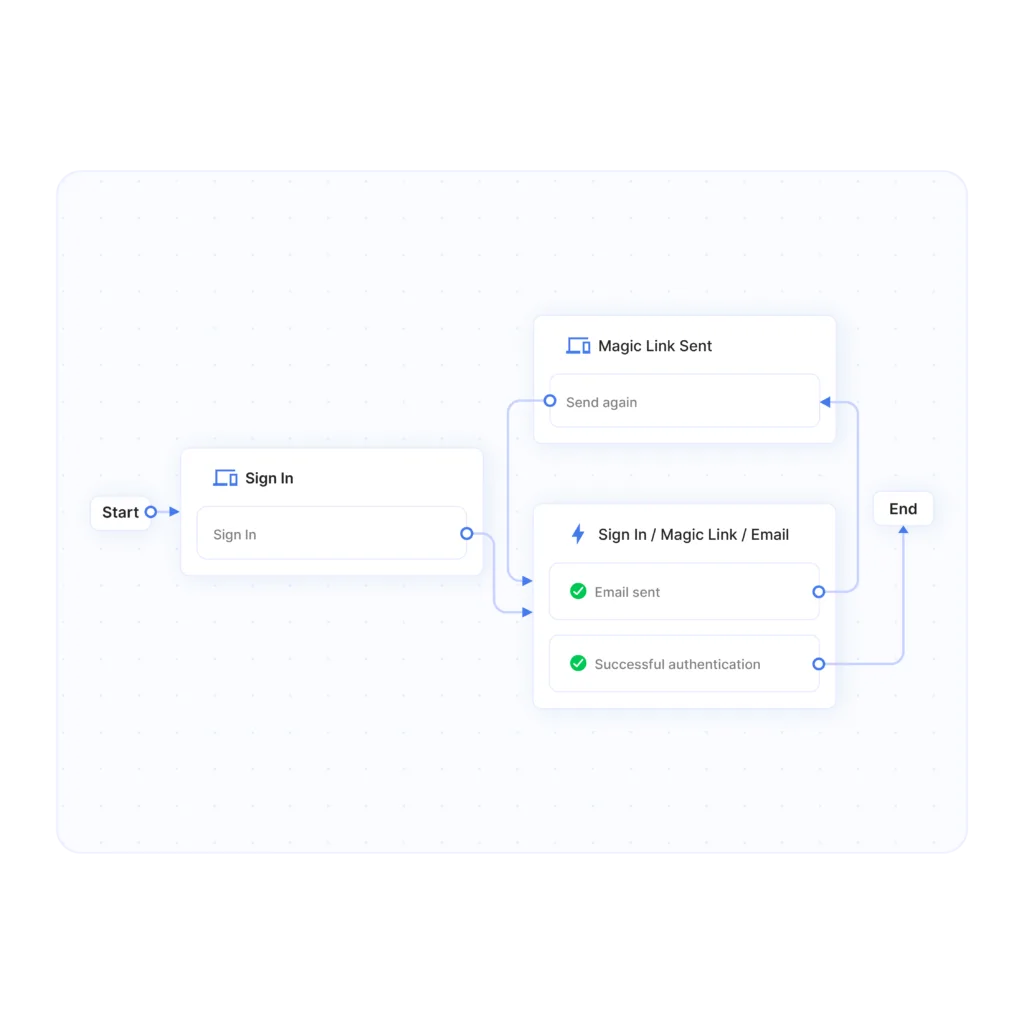
For businesses looking to scale, seamless and secure customer authentication is a must. Descope simplifies this with a fully managed, no-code CIAM platform that enhances security and user experience—without the complexity of traditional solutions.
How Descope Simplifies & Strengthens Authentication
Descope offers an intuitive drag-and-drop workflow builder that allows businesses to seamlessly integrate security into their applications—without deep coding expertise. This no-code/low-code approach enables teams to design and deploy authentication flows in minutes, rather than weeks, reducing development time and operational overhead.
With pre-built authentication modules, developers can:
- Implement passwordless authentication using biometrics, passkeys, and magic links.
- Configure adaptive MFA that triggers based on user behavior and risk levels.
- Set up risk-based access control to prevent fraudulent login attempts.
By removing the need for custom authentication logic, Descope simplifies security implementation while providing enterprises with the flexibility to tailor authentication experiences based on their users’ needs.
Unlocking Business Potential: Where Companies Can Leverage Descope
Descope’s authentication solutions are versatile and can be applied at multiple critical points in a company’s digital ecosystem:
1. User Onboarding & Registration
- Implement frictionless sign-ups using social logins, biometrics, or magic links, reducing abandonment rates.
- Use progressive profiling to collect user information over time instead of lengthy registration forms.
2. Login & Access Management
- Enable passwordless logins across web and mobile apps, enhancing convenience and security.
- Apply adaptive MFA to high-risk logins while keeping low-risk logins seamless.
3. Account Recovery & Reauthentication
- Reduce account recovery friction with secure magic links and biometric reauthentication, eliminating the hassle of password resets.
- Enable step-up authentication for sensitive actions, such as profile updates or transaction approvals.
4. Fraud Prevention & Risk Mitigation
- Use behavioral analytics, IP reputation checks, and device fingerprinting to detect suspicious login patterns.
- Implement risk-based access control that adapts security measures based on real-time threats.
5. Compliance & Security Enhancements
- Meet regulatory requirements (e.g., GDPR, CCPA, PSD2) with built-in security and audit logging.
- Ensure end-to-end encryption of user credentials, reducing the risk of data breaches.
Real-World Success: Businesses Leveraging Descope
Companies across industries use Descope to enhance security and streamline authentication, improving user experience and engagement.
- Branch Insurance – Reduced auth-related support tickets by 50% with passkey authentication.
- Navan (formerly TripActions) – Deployed strong MFA in just 4 days for enhanced security.
- GradRight – Prevented OTP bot attacks while enabling secure student onboarding.
- AEG Presents – Implemented email OTP authentication for secure festival ticket verification.
Descope helps businesses scale securely, reducing friction while improving fraud prevention and compliance.
The Final Word: Secure, Scale, and Succeed with CIAM
In today’s digital battleground, secure customer authentication isn’t just about protection—it’s about survival. CIAM isn’t a luxury; it’s the backbone of business growth, ensuring airtight security, seamless customer experiences, and ironclad fraud prevention. As companies scale, the real challenge is balancing bulletproof authentication with frictionless user journeys.
For businesses that refuse to compromise, Descope CIAM delivers. Built for the future, it offers the perfect mix of security, scalability, and effortless integration—so you can focus on growth while keeping threats at bay. Because in a world where trust is currency, your authentication strategy is everything.
Find out more about Descope, or reach out to an expert at cpaas-sales@8×8.com.




