In today’s fast-paced digital world, the importance of secure verification systems cannot be overstated. Businesses face growing cybersecurity threats that endanger sensitive information, user data, and overall trust. Weak verification measures open the door to unauthorized access, fraud, and data breaches, leading to significant financial and reputational damage. As cyber-attacks and identity theft become more sophisticated, having a robust verification process is no longer a luxury; it’s a necessity.
Effective verification processes are essential for tasks such as onboarding new customers, securing transactions, and preventing fraud. By confirming that users are who they claim to be, businesses can safeguard sensitive data, reduce the risk of unauthorized access, and build trust with their customers. A strong verification system not only helps in maintaining the integrity of your operations but also enhances the overall user experience by preventing potential security breaches and ensuring smooth interactions.
Why Robust Verification Matters in the Digital Age
Cybersecurity Threats Are Rising
Cyber-attacks and data breaches are not just a concern for large corporations anymore. Small and medium-sized businesses are equally vulnerable, if not more so. The rise of cybersecurity threats, including phishing, malware, and identity theft, means that businesses must prioritize strong verification systems. Hackers are constantly devising new ways to exploit weak security systems, often targeting businesses with inadequate protection measures, according to the global threat report from Crowdstrike. Inadequate verification processes lead to unauthorized access, where attackers can steal sensitive customer data, financial information, and intellectual property. This can result in both immediate financial loss and long-term reputational damage.
Trust and Compliance
Beyond security, having a strong verification process is crucial for building customer trust. Users today are more security-conscious than ever and are likely to abandon platforms that seem insecure. By implementing secure verification processes, businesses not only protect themselves but also reassure their customers that their data is safe.
Additionally, various industries are now subject to strict regulatory requirements, such as GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the United States. These regulations mandate businesses to take concrete steps in protecting user data. Failure to comply with these regulations can result in hefty fines and legal consequences. Having a robust verification process can help businesses meet these compliance standards by ensuring that only authorized individuals access sensitive information.
Customer Experience
While security is critical, user experience also matters. Complex or intrusive verification processes can frustrate users, leading to high abandonment rates. The key is to strike the right balance between security and convenience. Authentication methods such as Silent Mobile Authentication allow businesses to provide a secure yet seamless user experience. With the right verification process , customers can quickly verify their identity without jumping through unnecessary hoops, keeping them engaged while ensuring their safety.
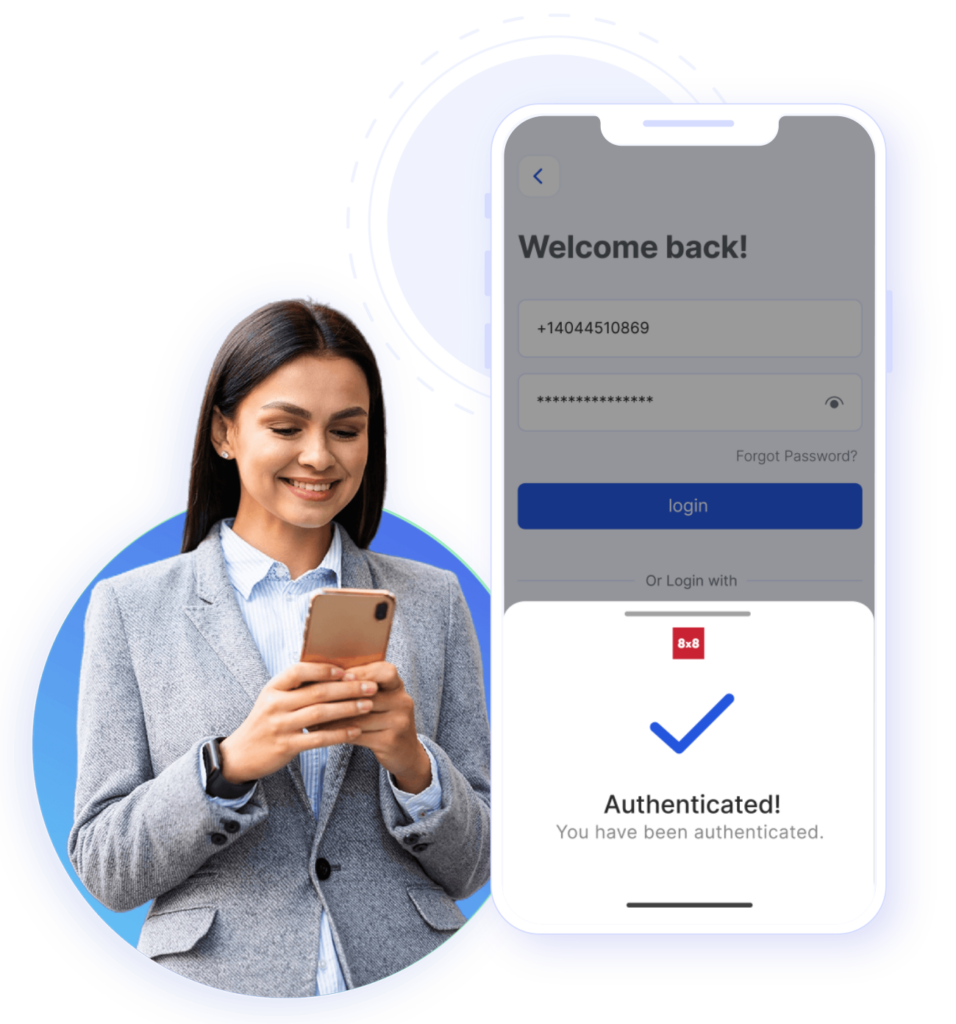
What is 8×8 Verification API?
Real-Time Identity Verification for Enhanced User Security
8×8 Verification API is a powerful tool designed to enhance user security by allowing businesses to verify the identities of their users in real time. Through this API, companies can send verification codes to users via SMS or other messaging channels like WhatsApp or Viber, or via Silent Mobile Authentication. These codes are used to confirm that the person accessing the account or performing a transaction is indeed the rightful user.
The 8×8 Verification API works by integrating with a business’s existing systems, enabling a streamlined verification process. For example, when a user attempts to log in or perform a sensitive action, the API sends a code to their registered phone number. The user then enters this code, which verifies their identity. This additional security layer makes it difficult for unauthorized users to gain access, even if they have stolen passwords or login credentials.
Versatile Applications Across Industries
The 8×8 Verification API can be used across multiple industries to enhance security. For example:
- E-commerce: Businesses can use 8×8 Verification API to secure customer accounts during login or purchase, protecting against fraudulent transactions.
- Banking and Finance: Financial institutions can verify users before allowing them to access sensitive account information or authorize large transactions.
- Healthcare: Hospitals and healthcare providers can ensure that only authorized personnel access patient data, safeguarding privacy and complying with regulations like HIPAA.
Benefits of Using 8×8 Verification API for Businesses
Improved Security
The primary benefit of implementing 8×8 Verification API is improved security. Businesses that rely on password-only authentication are at risk, as passwords can be easily stolen or guessed. 8×8 Verification API adds an additional layer of protection, making it harder for hackers to gain unauthorized access.
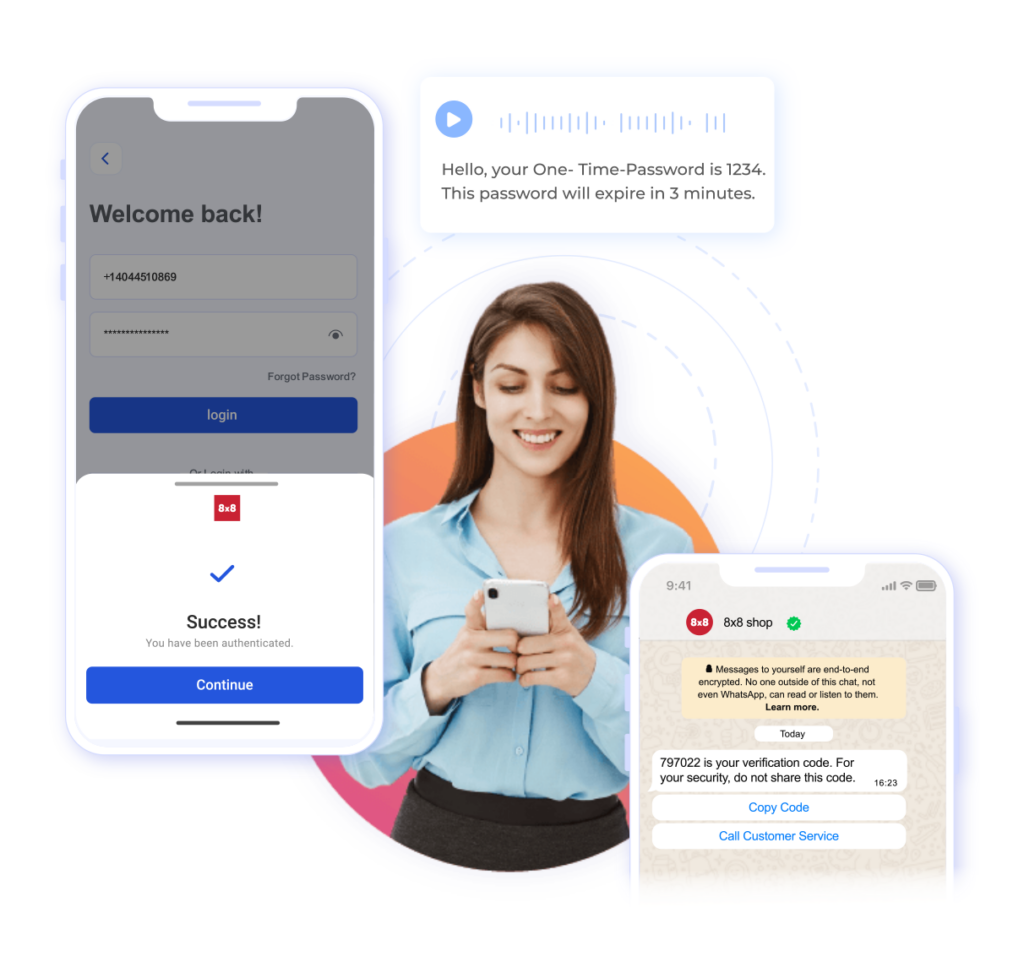
For example, using two-factor authentication (2FA) via SMS verification ensures that even if a password is compromised, the attacker would still need access to the user’s mobile phone to complete the login process.
Streamlined Authentication
While robust security is essential, businesses must also ensure that their verification processes are user-friendly. The 8×8 Verification API provides a streamlined authentication experience, allowing users to verify their identity quickly and efficiently. OTP SMS codes and 2FA are easy to use, and customers appreciate the added layer of security without feeling burdened by a complex verification process. You can even go a step further with Silent Mobile Authentication, which verifies the user’s identity quietly in the background using data like SIM card information, without interrupting the user at all.
Cost-Effectiveness
One of the significant advantages of adopting 8×8 Verification API is its cost-effectiveness. For many businesses, the cost of developing and managing these systems in-house outweighs the benefits.
With 8×8 Verification API, you only pay for successful verifications, ensuring that each authentication directly contributes to enhanced security and customer satisfaction. This pay-as-you-go model allows businesses to maximize their ROI, as costs are aligned with actual usage and effectiveness. This makes it an attractive option not just for startups, but also for established companies looking to streamline their verification processes while keeping costs under control.
Scalability
As businesses grow, their security needs evolve. 8×8 Verification API is highly scalable, meaning it can handle increasing numbers of users and verification requests without compromising performance or security. This is especially important for businesses experiencing rapid growth, as they need a system that can grow with them. 8×8’s Verification API is designed to meet the needs of businesses at any stage, offering customizable options that scale based on demand.
Key Features to Look for in a Verification API
When evaluating different Verification APIs, businesses should consider several essential features:
- End-to-End Management: Businesses should ensure that their systems can handle the complete verification process, including generating and sending OTP codes, as well as validating these codes in real-time. This approach provides users with a fast and secure method to verify their identities, enhancing both security and user experience.
- Customizability & Scalability: The Verification API should be customizable to meet the specific needs of the business and scalable to handle increased verification demands as the business grows.
- Ease of Integration: Look for an API that is easy to integrate into your existing systems. 8×8’s Verification API provides clear documentation and support to ensure a smooth integration process.
- Guaranteed Deliverability: Opt for an API that automatically switches to voice messages when SMS or WhatsApp encounters issues. This guarantees users receive their verification codes promptly and reliably, enhancing the overall user experience and boosting conversion rates
- Performance Tracking: Choose an API that provides comprehensive dashboards to monitor message delivery, conversion rates, and overall performance, enabling continuous optimization of deliverability and user satisfaction
- Multi-Channel OTP: Enhance your verification process with support for one-time passwords sent via SMS, WhatsApp, Viber, or voice
Conclusion: Secure Your Business with Robust Verification
In the digital age, strong verification systems are essential for protecting both your business and your customers from cyber threats. The 8×8 Verification API provides an effective solution by offering advanced security features, seamless integration, and scalability. Whether you’re concerned about unauthorized access, fraud, or compliance, a reliable verification process can help safeguard your operations.
Don’t wait for a security breach to realize the importance of strong verification measures. Start exploring how 8×8’s Verification API can meet your business’s security needs and help you stay ahead in an increasingly dangerous digital world. Find out more here or reach out to an expert at cpaas-sales@8×8.com to find out more.




